If I Upload a Page From a Non Https to My Domain Which Is Https Will I Still Be Secure
Setting up HTTPS can exist a chip intimidating for the inexperienced user — it takes many steps with dissimilar parties, it requires specific knowledge of encryption and server configuration, and information technology sounds complicated in general.
A Comprehensive Guide To HTTP/ii Server Push button
In this related article, you lot'll learn all nearly server push, from how it works to the problems it solves. Y'all'll learn how to apply it, how to tell if it'due south working, and its impact on performance. Read a related commodity →
In this guide, I will explicate the individual components and steps and will clearly cover the individual stages of the setup. Your experience should exist piece of cake, peculiarly if your hosting provider as well supplies HTTPS certificates — chances are you will exist able to perform everything from your control panel quickly and hands.
I have included detailed instructions for owners of shared hosting plans on cPanel, administrators of Apache HTTP servers and of Nginx on Linux and Unix, equally well as Internet Information Server on Windows.
Permit's kickoff with the nuts.
More later on jump! Continue reading below ↓
HTTP Vs. HTTPS Vs. HTTP/2 Vs. SSL Vs. TLS: What'south What?
A lot of acronyms are used to describe the processes of communication between a client and a server. These are often mixed up by people who are not familiar with the internals.
The Hypertext Transfer Protocol (HTTP) is the bones communication protocol that both clients and servers must implement in gild to exist able to communicate. It covers things such as requests and responses, sessions, caching, authentication and more. Work on the protocol, as well every bit on the Hypertext Markup Language (HTML), started in 1989 by Sir Tim Berners-Lee and his team at CERN. The kickoff official version of the protocol (HTTP one.0) was released in 1996, soon followed by the currently widely adopted version (HTTP 1.1) in 1997.
The protocol transfers data between the browser and the server in articulate text, allowing the network, through which the data passes, to see the data transmitted. This is a security concern, so HTTP Secure (HTTPS) was introduced, allowing the client and the server to starting time establish an encrypted communication aqueduct, and and then pass the articulate text HTTP letters through it, effectively protecting them from eavesdropping.
The encrypted channel is created using the Transport Layer Security (TLS) protocol, previously called Secure Socket Layer (SSL). The terms SSL and TLS are often used interchangeably, with SSL 3.0 being replaced by TLS 1.0. SSL was a Netscape-developed protocol, while TLS is an IETF standard. At the time of writing, all versions of SSL (1.0, ii.0, 3.0) are deprecated due to various security bug and will produce warnings in current browsers, and the TLS versions (1.0, 1.1, 1.two) are in employ, with 1.3 currently a draft.
So, former effectually 1996 and 1997, we got the current stable version of the Net (HTTP 1.i, with or without SSL and TLS), which still powers the majority of websites today. Previously, HTTP was used for not-sensitive traffic (for example, reading the news), and HTTPS was used for sensitive traffic (for example, authentication and east-commerce); withal, increased focus on privacy means that web browsers such as Google Chrome now mark HTTP websites as "not private" and will introduce warnings for HTTP in future.
The next upgrade of the HTTP protocol — HTTP/2 — which is existence adopted by a growing number of websites, adds new features (pinch, multiplexing, prioritization) in order to reduce latency and increase performance and security.
In HTTP version 1.1, the secure connexion is optional (y'all may have HTTP and/or HTTPS contained of each other), while in HTTP/2 it is practically mandatory — even though the standard defines HTTP/2 with or without TLS, most browser vendors have stated that they volition just implement support for HTTP/ii over TLS.
What Does HTTPS Provide?
Why carp with HTTPS in the first place? Information technology is used for three main reasons:
- Confidentiality. This protects the communication betwixt two parties from others within a public medium such as the Net. For example, without HTTPS, someone running a Wi-Fi access signal could encounter private data such as credit cards when someone using the access indicate purchases something online.
- Integrity. This makes sure information reaches its destined party in full and unaltered. For case, our Wi-Fi friend could add extra advertisements to our website, reduce the quality of our images to salve bandwidth or change the content of articles we read. HTTPS ensures that the website can't be modified.
- Authentication. This ensures that the website is really what it claims to be. For example, that same person running the Wi-Fi access point could send browsers to a fake website. HTTPS ensures that a website that says it's
example.comis reallyinstance.com. Some certificates fifty-fifty check the legal identity behind that website, and then that you knowyourbank.comis YourBank, Inc.
Cryptography In A Nutshell
Confidentiality, integrity and authentication aren't HTTPS-specific: They're the core concepts of cryptography. Let'south expect a little more than closely at them.
Confidentiality
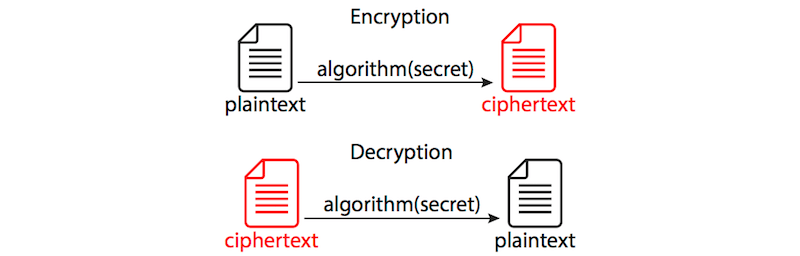
Confidentiality is privacy — that is, it protects information from being read by an unauthorized third party. The procedure unremarkably involves turning a readable (i.due east. aural and visible) form of the information, chosen plaintext, into a scrambled, unreadable version, chosen ciphertext. This process is chosen encryption. The reverse procedure — turning the unreadable ciphertext back into readable plaintext — is called decryption. In that location are many methods — nothing functions (or algorithms) — to encrypt and decrypt information.
In society for two parties to be able to communicate, they should agree on ii things:
- which algorithm (cipher function) they will use in their communication;
- which parameters, countersign or rules (i.east. secret) volition exist used with the method selected.
There are two main types of encryption methods:
- symmetric. Both parties share a common secret key.
- asymmetric. 1 of the parties has a pair of a underground and a public cardinal, the foundation of public key infrastructure (PKI).
The symmetric class of methods relies on both parties having a shared secret, which the sender uses to encrypt the data, which in turn the receiver decrypts using the same method and key (see the figure below). The problem with these methods is how both parties will negotiate (i.eastward. exchange) the secret without physically meeting each other — they demand to have a secure advice channel of some sort.
The asymmetric methods come up to solve this kind of problem — they are based on the notion of public and private keys. The plaintext is encrypted using one of the keys and tin can only be decrypted using the other complementary key.
So, how does it piece of work? Let's assume we take two parties who are willing to communicate with each other securely — Alice and Bob (these are always the names of the fictional characters in every tutorial, security transmission and the similar, so we'll award the tradition hither every bit well). Both of them take a pair of keys: a individual key and a public 1. Private keys are known only to their respective owner; public keys are available to anyone.
If Alice wants to send a message to Bob, she would obtain his public key, encrypt the plaintext and ship him the ciphertext. He would then use his own private key to decrypt it.
If Bob would similar to send a respond to Alice, he would obtain her public central, encrypt the plaintext and send her the ciphertext. She would and then utilize her own individual cardinal to decrypt it.
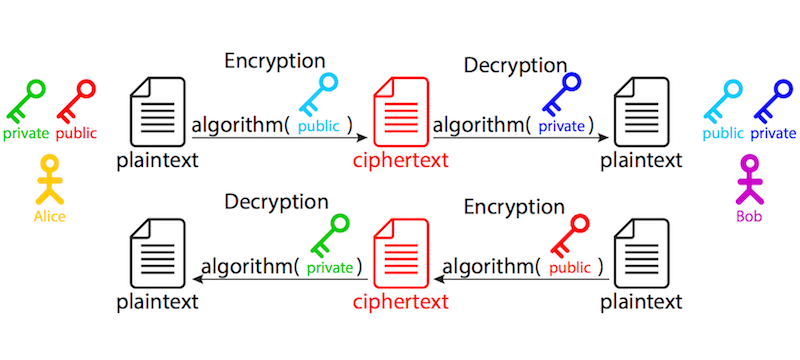
When do nosotros use symmetric and when do we utilise disproportionate encryption? Disproportionate encryption is used to exchange the secret between the customer and the server. In real life, we usually do not need two-way asymmetric communication — information technology is sufficient if one of the parties (we'll just call it a server, for the sake of simplicity) has the set of keys, so information technology can receive an encrypted message. Information technology really protects the security of information in simply one management — from the client to the server, because the information encrypted with the public key can only be decrypted using the private central; hence, merely the server tin can decrypt it. The other direction is non protected — information encrypted with the server's private fundamental tin be decrypted with its public primal past anyone. The other political party (we'll similarly telephone call it a customer) begins the communication by encrypting a randomly generated session cloak-and-dagger with the server's public primal, then sends the ciphertext back to the server, which, in turn, decrypts it using its own private key, now having the secret.
Symmetric encryption is and then used to protect the bodily data in transit, since information technology'southward much faster than asymmetric encryption. The two parties (the customer and the server), with the previously exchanged secret, are the only ones able to encrypt and decrypt the information.
That's why the offset asymmetric part of the handshake is too known (and referred to) every bit fundamental exchange and why the actual encrypted advice uses algorithms known (and referred to) as cipher methods.
Integrity
Another concern, solved with HTTPS, is information integrity: (i) whether the entire data arrived successfully, and (2) whether it was modified by someone in transit. In order to ensure the data is transmitted successfully, message assimilate algorithms are used. Computing message authentication codes (MACs) for each message exchanged are a cryptographic hashing procedure. For example, obtaining a MAC (sometimes called a tag) uses a method that ensures that information technology is practically incommunicable (the term ordinarily used is infeasible) to:
- change the bulletin without affecting the tag,
- generate the aforementioned tag from 2 different messages,
- reverse the procedure and obtain the original message from the tag.
Authentication
What well-nigh hallmark? The trouble with the real-life application of the public key infrastructure is that both parties take no way of knowing who the other party actually is — they are physically split up. In order to testify the identity of the other party, a mutually trusted third party — a document authorisation (CA) — is involved. A CA issues a certificate, stating that the domain name example.com (a unique identifier), is associated with the public key XXX. In some cases (with EV and OV certificates — run across below), the CA will also bank check that a particular visitor controls that domain. This information is guaranteed by (i.e. certified by) the certificate authorisation X, and this guarantee is valid no earlier than (i.eastward. begins on) date Y and no afterwards than (i.e. expires on) date Z. All of this information goes into a unmarried document, called an HTTPS certificate. To present an easily understandable analogy, information technology is similar a country government (a third party trusted by all) issuing an ID or a passport (a certificate) to a person — every party that trusts the regime would likewise accept the identity of the ID holder (assuming the ID is not imitation, of course, simply that's outside the scope of this example).
Certification regime (CAs) are organizations trusted to sign certificates. Operating systems, such as Windows, macOS, iOS and Android, besides as the Firefox browser, accept a listing of trusted certificates.
Y'all can bank check which CAs are trusted by your browser:
- Firefox "Options" → "Advanced" → "Certificates" → "View Certificates" → "Authorities"
- Windows "Control Panel" → "Internet Options" → "Content" — "Certificates" → "Trusted Root Certification Authorities / Intermediate Certification Authorities"
- Mac "Applications" → "Utilities" → "Keychain Access." Under "Category," pick Certificates"
All certificates are and so checked and trusted — by the operating system or browser if directly trusted or past a trusted entity if verified. This mechanism of transitive trust is known as a chain of trust:
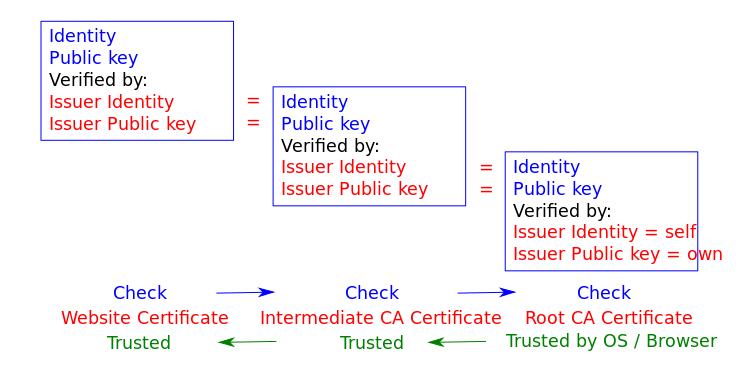
You can add other unlisted CAs, which is useful when working with self-signed certificates (which we'll discuss later).
In most common situations, simply the server needs to be known to the client — for instance, an due east-commerce website to its customers — so, only the website needs a certificate. In other situations, such as e-authorities systems, both the server and the customer, requesting a service, should have their identity proven. This ways that both parties should be using certificates to cosign to the other political party. This setup is too outside the scope of this article.
Types Of HTTPS Certificates
There are several types of HTTPS certificates. They tin can exist categorized according to the following criteria.
1. Identity Validation
- Domain validated (DV) The nigh common type of certificate, a DV document verifies that the domain matches a particular public key. The browser establishes a secure connection with the server and displays the closed padlock sign. Clicking the sign will show "This website does not supply ownership information." There are no special requirements other than having a domain — a DV certificate simply ensures that this is the right public cardinal for that domain. The browser does not evidence a legal entity. DV certificates are oft cheap (10 USD per year) or free — run into the sections on Let's Encrypt and Cloudflare below.
- Extended validation (EV) EV certificates verify the legal organisation behind a website. This is the nigh trustworthy type of document, which is obtained after a CA checks the legal entity that controls the domain. The legal entity is checked with a combination of:
- control of the domain (such every bit a DV certificate);
- government business records, to make certain the company is registered and active;
- independent concern directories, such as Dunn and Bradstreet, Salesforce'south connect.data.com, Yellow Pages, etc.;
- a verification phone call;
- inspection of all domain names in the certificate (wildcards are explicitly forbidden for EV certificates).Equally well as the closed padlock sign, EV HTTPS certificates display the name of the validated legal entity — typically a registered company — before the URL. Some devices, such as iOS Safari, will but show the validated legal entity, ignoring the URL completely. Clicking the sign will testify details well-nigh the organisation, such as the proper noun and street accost. The cost is between 150 and 300 USD per year.
- System validated (OV) Like EV, OV certificates verify the legal organization behind a website. Yet, dissimilar EV, OV HTTPS certificates practise not brandish the verified legal name in the UI. As a result, OV certificates are less popular, because they have high validation requirements, without the benefits of these beingness shown to users. Prices are in the 40 to 100 USD per year range.
two. Number of Domains Covered
One time upon a time, HTTPS certificates mostly contained a single domain in the CN field. Afterwards, the "subject culling proper name" (SAN) field was added to permit additional domains to be covered by a unmarried certificate. These days, all HTTPS certificates are created equal: Even a unmarried-domain certificate will have a SAN for that unmarried domain (and a second SAN for the world wide web version of that domain). However, many document vendors notwithstanding sell unmarried- and multi-domain HTTPS certificates for historical reasons.
- Single domain This is the almost common type of certificate, valid for the domain names
example.comandworld wide web.example.com. - Multiple domains (UCC/SAN) This type of certificate, also known as Unified Communications Certificate (UCC) or Field of study Alternative Names (SAN) document, tin cover a list of domains (up to a sure limit). It is not express to a single domain — y'all can mix dissimilar domains and subdomains. The price ordinarily includes a prepare number of domains (three to 5), with the option to include more than (up to the limit) for an additional fee. Using information technology with related websites is brash, considering the client inspecting the certificate of any of the websites volition see the main domain, likewise as all additional ones.
- Wildcard This type of certificate covers the master domain likewise every bit an unlimited number of subdomains (
*.case.com) — for example,example.com,www.example.com,post.example.com,ftp.example.com, etc. The limitation is that it covers only subdomains of the main domain.
The variety of HTTPS certificates available is summarized in the table below:
| Certificate type | Domain validated (DV) | Organization validated (OV) | Extended validation (EV) |
|---|---|---|---|
| HTTPS | HTTPS Verified legal owner | HTTPS Verified legal possessor Owner info displayed in browser | |
| Single domain | case.com, www.instance.com | ||
| Multiple domains | case.com, www.example.com, mail.example.com, example.net, instance.org, etc. predefined list, up to a sure limit (usually 100) | ||
| Wildcard | *.case.com matches any subdomain | N/A — all names must exist included explicitly in the certificate and inspected by the CA. | |
The Configuration
To recap, four components of HTTPS require encryption:
- The initial key substitution This uses asymmetric (private and public fundamental) algorithms.
- The identity certification (the HTTPS certificate, issued past a certification authority) This uses asymmetric (private and public primal) algorithms.
- The actual message encryption This uses symmetric (pre-shared undercover) algorithms.
- The message digesting This uses cryptographic hashing algorithms.
Each of these components has a fix of used algorithms (some of them deprecated already) that use different key sizes. Part of the handshake involves the client and the server agreeing on which combination of methods they will apply — select one out of virtually a dozen public key (fundamental exchange) algorithms, one out of about a dozen symmetric key (cipher) algorithms and one out of three (two deprecated) message-digesting (hashing) algorithms, which gives us hundreds of combinations.
For case, the setting ECDHE-RSA-AES256-GCM-SHA384 means that the key will be exchanged using the Elliptic Curve Diffie-Hellman Ephemeral (ECDHE) primal exchange algorithm; the CA signed the certificate using the Rivest-Shamir-Adleman (RSA) algorithm; the symmetric bulletin encryption will utilize the Advanced Encryption Standard (AES) naught, with a 256-flake key and GCM style of operation; and bulletin integrity will be verified using the SHA secure hashing algorithm, using 384-bit digests. (A comprehensive list of algorithm combinations is available.)
So, in that location are some configuration choices to be fabricated.
Zilch Suites
Deciding the cipher suites to use is a residue between compatibility and security:
- Compatibility with older browsers needs the server to support older cypher suites.
- All the same, many older zilch suites are no longer considered secure.
OpenSSL lists the supported combinations (run across above) in order of cryptographic force, with the most secure at the top and the weakest at the lesser. It is designed in this mode because, during the initial handshake between the customer and the server, the combination to be used is negotiated until a match is institute that is supported by both parties. It makes sense to first attempt the almost secure combinations and gradually resort to weaker security only if there is no other mode.
A very useful and highly recommended resources, advising on what cryptographic methods to enable on the server, is the Mozilla SSL Configuration Generator, which we'll utilize later on on with actual server configurations.
Cardinal Types
Elliptic Bend Cryptography (ECC) certificates are faster and utilise less CPU than the RSA certificates, which is especially important for mobile clients. All the same, some services, such as Amazon, CloudFront and Heroku, don't notwithstanding, at the time of writing, support ECC certificates.
A 256-bit ECC key is considered sufficient.
Rivest Shamir Adleman (RSA) certificates are slower but compatible with a wider multifariousness of older servers. RSA keys are larger, so a 2048-bit RSA primal is considered minimal. RSA certificates of 4096 and above may hurt performance — they're also probable to exist signed past a 2048-bit intermediary, undermining much of the additional security!
Y'all might take noticed the fluidity of the statements above and the lack of whatever numbers — it is because what is a heavy load on 1 server is not on some other. The best way to decide the touch on on operation is to monitor the load on your server, with your real website(s) and your real visitors. And even that will modify over fourth dimension.
Procedures
To obtain an HTTPS certificate, perform the post-obit steps:
- Create a private and public key pair, and fix a Certificate Signing Request (CSR), including information most the organisation and the public key.
- Contact a certification authority and request an HTTPS certificate, based on the CSR.
- Obtain the signed HTTPS certificate and install it on your spider web server.
At that place exists a ready of files, containing different components of the public key infrastructure (PKI): the private and public keys, the CSR and the signed HTTPS document. To make things even more complicated, different parties use different names (and file extensions) to identify one and the same thing.
To start, there are two pop formats for storing the data — DER and PEM. The start one (DER) is binary, and the 2d (PEM) is a base64-encoded (text) DER file. By default, Windows uses the DER format directly, and the open up-source world (Linux and UNIX) uses the PEM-format. At that place are tools (OpenSSL) to convert betwixt 1 and the other.
The files nosotros'll exist using as examples in the process are the following:
-
example.com.centralThis PEM-formatted file contains the private key. The extension.centralis not a standard, then some might use information technology and others might not. It is to be protected and attainable only past the system super-user. -
case.com.pubThis PEM-formatted file contains the public primal. You do not actually need this file (and it'southward never explicitly present), because it tin can be generated from the private primal. It is merely included hither for analogy purposes. -
example.com.csrThis is a certificate signing asking. A PEM-formatted file containing organizational information, every bit well as the server's public cardinal, should be sent to the certification authority issuing the HTTPS certificate. -
instance.com.crtThis HTTPS certificate is signed by the certification authority. It is a PEM-formatted file, including the server'southward public primal, organizational information, the CA signature, validity and expiry dates, etc. The extension.crtis not a standard; other common extensions include.certand.cer.
File names (and extensions) are not standard; they tin exist annihilation you like. I have called this naming convention because I call up it is illustrative and makes more obvious which component has what role. Y'all tin use whatsoever naming convention makes sense to you, as long every bit y'all refer to the appropriate primal-certificate files in the commands and server configuration files throughout the process.
The private key is a randomly generated string of a certain length (nosotros'll use 2048-bit), which looks like the post-obit:
-----Begin RSA Private KEY----- MIIEowIBAAKCAQEAm+036O2PlUQbKbSSs2ik6O6TYy6+Zsas5oAk3GioGLl1RW9N i8kagqdnD69Et29m1vl5OIPsBoW3OWb1aBW5e3J0x9prXI1W/fpvuP9NmrHBUN4E S17VliRpfVH3aHfPC8rKpv3GvHYOcfOmMN+HfBZlUeKJKs6c5WmSVdnZB0R4UAWu Q30aHEBVqtrhgHqYDBokVe0/H4wmwZEIQTINWniCOFR5UphJf5nP8ljGbmPxNTnf b/iHS/chjcjF7TGMG36e7EBoQijZEUQs5IBCeVefOnFLK5jLx+BC//X+FNzByDil Tt+l28I/3ZN1ujhak73YFbWjjLR2tjtp+LQgNQIDAQABAoIBAEAO2KVM02wTKsWb dZlXKEi5mrtofLhkbqvTgVE7fbOKnW8FJuqCl+2NMH31F1n03l765p4dNF4JmRhv /+ne4vCgOPHR/cFsH4z/0d5CpHMlC7JZQ5JjR4QDOYNOpUG51smVamPoZjkOlyih XGk/q72CxeU6F/gKIdLt6Dx03wBosIq9IAE8LwdMnioeuj18qaVg195OMeIOriIn tpWP4eFya5rTpIFfIdHdIxyXsd6hF/LrRc9BMWTY1/uOLrpYjTf7chbdNaxhwH7k buvKxBvCvmXmd6v/AeQQAXbUkdSnbTKDaB9B7IlUTcDJyPBJXvFS1IzzjN6vV+06 XBwHx5ECgYEAyRZLzwnA3bw8Ep9mDw8JHDQoGuQkFEMLqRdRRoZ+hxnBD9V9M0T6 HRiUFOizEVoXxf6zPtHm/T7cRD8AFqB+pA/Nv0ug6KpwUjA4Aihf5ADp0gem0DNw YlVkCA6Bu7c9IUlE0hwF7RLB7YrryJVJit9AymmUTUUHCQTWW2yBhC8CgYEAxoHS HGXthin5owOTNPwLwPfU2o7SybkDBKyW69uTi0KxAl3610DjyA/cV2mxIcFlPv1y HualGd9eNoeCMBy/AUtjzI0K77yeRpjj321rj6k8c8bYWPHH539SiBXLWTY/WQ0w pxfT3d/Z4QMh5d6p+p5f3UIrXESYQd+fAaG5tNsCgYEAksTdTB4YUT9EsWr6eN9G jPlclFQUKV3OMvq77bfYvg8EJORz32nnDDmWS7SUjoOtemwutBlMeWbaKk25aMp3 5JNMXuV6apeMJ9Dd8GU7qBUqlIvVK31/96XPvzmnYzWZPqRVwO2HPcRFG3YcJmkg JmZQyexJvCQ3wFNxiYUm+y0CgYBXQSMhFnCUg4jWbbDcHlnwRT+LnjHrN2arPE3O eKLfGL6DotmqmjxFaStaRPv2MXMWgAMUsB8sQzG/WEsSaOBQaloAxJJlFIyhzXyE bi1UZXhMD8BzQDu1dxLI/IN4wE6SDykumVuocEfuDxlsWDZxEgJjWD2E/iXK9seG yRa+9wKBgEydVz+C1ECLI/dOWb20UC9nGQ+2dMa+3dsmvFwSJJatQv9NGaDUdxmU hRVzWgogZ8dZ9oH8IY3U0owNRfO65VGe0sN00sQtMoweEQi0SN0J6FePiVCnl7pf lvYBaemLrW2YI2B7zk5fTm6ng9BW/B1KfrH9Vm5wLQBchAN8Pjbu -----Cease RSA Individual Central----- Go on the private key private! This means protect it by very restricted permissions (600), and practice not disembalm it to anyone.
Its counterpart — the public key — looks like this:
-----Brainstorm PUBLIC Primal----- MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAm+036O2PlUQbKbSSs2ik 6O6TYy6+Zsas5oAk3GioGLl1RW9Ni8kagqdnD69Et29m1vl5OIPsBoW3OWb1aBW5 e3J0x9prXI1W/fpvuP9NmrHBUN4ES17VliRpfVH3aHfPC8rKpv3GvHYOcfOmMN+H fBZlUeKJKs6c5WmSVdnZB0R4UAWuQ30aHEBVqtrhgHqYDBokVe0/H4wmwZEIQTIN WniCOFR5UphJf5nP8ljGbmPxNTnfb/iHS/chjcjF7TGMG36e7EBoQijZEUQs5IBC eVefOnFLK5jLx+BC//X+FNzByDilTt+l28I/3ZN1ujhak73YFbWjjLR2tjtp+LQg NQIDAQAB -----Finish PUBLIC Fundamental----- The Certificate Signing Asking (CSR) looks like the following:
-----BEGIN CERTIFICATE REQUEST----- MIICzjCCAbYCAQAwgYgxFDASBgNVBAMMC2V4YW1wbGUuY29tMQswCQYDVQQLDAJJ VDEPMA0GA1UECAwGTG9uZG9uMRIwEAYDVQQKDAlBQ01FIEluYy4xIDAeBgkqhkiG 9w0BCQEWEWFkbWluQGV4YW1wbGUuY29tMQswCQYDVQQGEwJHQjEPMA0GA1UEBwwG TG9uZG9uMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAm+036O2PlUQb KbSSs2ik6O6TYy6+Zsas5oAk3GioGLl1RW9Ni8kagqdnD69Et29m1vl5OIPsBoW3 OWb1aBW5e3J0x9prXI1W/fpvuP9NmrHBUN4ES17VliRpfVH3aHfPC8rKpv3GvHYO cfOmMN+HfBZlUeKJKs6c5WmSVdnZB0R4UAWuQ30aHEBVqtrhgHqYDBokVe0/H4wm wZEIQTINWniCOFR5UphJf5nP8ljGbmPxNTnfb/iHS/chjcjF7TGMG36e7EBoQijZ EUQs5IBCeVefOnFLK5jLx+BC//X+FNzByDilTt+l28I/3ZN1ujhak73YFbWjjLR2 tjtp+LQgNQIDAQABoAAwDQYJKoZIhvcNAQELBQADggEBAGIQVhXfuWdINNfceNPm CkAGv4yzpx88L34bhO1Dw4PYWnoS2f7ItuQA5zNk9EJhjkwK8gYspK7mPkvHDbFa Um7lPSWsm3gjd3pU7dIaHxQ+0AW9lOw5ukiBlO4t3qgt+jTVZ3EhMbR0jDSyjTrY kTgfuqQrGOQSmLb5XviEtCcN0rseWib3fKIl8DM69JiA2AALxyk7DCkS1BqLNChT pnbgvtlUhc4yFXNCtwPGskXIvLsCn2LRy+qdsPM776kDLgD36hK0Wu14Lpsoa/p+ ZRuwKqTjdaV23o2aUMULyCRuITlghEEkRdJsaXadHXtNd5I5vDJOAAt46PIXcyEZ aQY= -----END CERTIFICATE REQUEST----- This particular CSR contains the server'south public primal and details about the organization Pinnacle Inc., based in London, UK, and which owns the domain name example.com.
Finally, the signed HTTPS certificate looks like the post-obit:
-----BEGIN Certificate----- MIIDjjCCAnYCCQCJdR6v1+W5RzANBgkqhkiG9w0BAQUFADCBiDEUMBIGA1UEAwwL ZXhhbXBsZS5jb20xCzAJBgNVBAsMAklUMQ8wDQYDVQQIDAZMb25kb24xEjAQBgNV BAoMCUFDTUUgSW5jLjEgMB4GCSqGSIb3DQEJARYRYWRtaW5AZXhhbXBsZS5jb20x CzAJBgNVBAYTAkdCMQ8wDQYDVQQHDAZMb25kb24wHhcNMTYwNDE5MTAzMjI1WhcN MTcwNDE5MTAzMjI1WjCBiDEUMBIGA1UEAwwLZXhhbXBsZS5jb20xCzAJBgNVBAsM AklUMQ8wDQYDVQQIDAZMb25kb24xEjAQBgNVBAoMCUFDTUUgSW5jLjEgMB4GCSqG SIb3DQEJARYRYWRtaW5AZXhhbXBsZS5jb20xCzAJBgNVBAYTAkdCMQ8wDQYDVQQH DAZMb25kb24wggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCb7Tfo7Y+V RBsptJKzaKTo7pNjLr5mxqzmgCTcaKgYuXVFb02LyRqCp2cPr0S3b2bW+Xk4g+wG hbc5ZvVoFbl7cnTH2mtcjVb9+k+iv/02ascFQ3gRLXtWWJGl9Ufdod88Lysqm/ca8 dg5x86Yw34d8FmVR4okqzpzlaZJV2dkHRHhQBa5DfRocQFWq2uGAepgMGiRV7T8f jCbBkQhBMg1aeII4VHlSmEl/mc/yWMZuY/E1Od9v+IdL9yGNyMXtMYwbfp7sQGhC KNkRRCzkgEJ5V586cUsrmMvH4EL/9f4U3MHIOKVO36Xbwj/dk3W6OFqTvdgVtaOM tHa2O2n4tCA1AgMBAAEwDQYJKoZIhvcNAQEFBQADggEBABwwkE7wX5gmZMRYugSS 7peSx83Oac1ikLnUDMMOU8WmqxaLTTZQeuoq5W23xWQWgcTtfjP9vfV50jFzXwat 5Ch3OQUS53d06hX5EiVrmTyDgybPVlfbq5147MBEC0ePGxG6uV+Ed+oUYX4OM/bB XiFa4z7eamG+Md2d/A1cB54R3LH6vECLuyJrF0+sCGJJAGumJGhjcOdpvUVt5gvD FIgT9B04VJnaBatEgWbn9x50EP4j41PNFGx/A0CCLgbTs8kZCdhE4QFMxU9T+T9t rXgaspIi7RA4xkSE7x7B8NbvSlgP79/qUe80Z7d8Oolva6dTZduByr0CejdfhLhi mNU= -----Stop Certificate----- All parts are connected and should match each other. The final certificate was generated for analogy purposes only — it is the so-chosen self-signed certificate, because it was non signed past a recognized certification authority.
The process will be illustrated with bodily steps for cPanel, Linux, FreeBSD and Windows. This is a universal process, valid for all kinds of certificates. If you lot are interested in getting a complimentary DV document, there are other procedures to follow in the sections on Permit'southward Encrypt and Cloudflare.
Stride 1: Create A Private Key And A Certificate Signing Asking (CSR)
In the post-obit examples, we'll use 2048-fleck RSA certificates, for their broad compatibility. If your server provider supports it (for case, if y'all don't use Heroku or AWS), you might prefer to apply ECC instead.
cPanel
- Log into your host's cPanel.
- Scroll down to the "Security" section and click "SSL/TLS."

cPanel "Security" section (View large version) - You lot are now in the "SSL/TLS Manager" dwelling house. Click "Private Keys (KEY)" to create a new private key.

cPanel "SSL/TLS Manager (View large version) - You will be redirected to a folio to "Generate, Paste or Upload a new "Private Key." Select "2048-scrap" in the "Fundamental Size" dropdown, and click "Generate."

cPanel "Private Primal" management (View big version) - The new private fundamental volition be generated, and you will get a confirmation screen:

cPanel private key confirmation (View large version) - If you go back to the "Private Keys" domicile, yous will see your new key listed:

cPanel "Individual Keys" with the new key generated (View big version) - Go back to the "SSL/TLS Manager" habitation. Click "Document Signing Requests (CSR)" to create a new certificate request.

cPanel "SSL/TLS Manager" (View big version) - You will at present exist presented with the "Generate Service Request" class. Select the previously created individual fundamental and fill up in the fields. Answer all of the questions correctly (they will be public in your signed certificate!), paying special attention to the "Domains" section, which should exactly match the domain name for which you are requesting the HTTPS certificate. Include the elevation-level domain only (
example.com); the CA volition commonly add thewwwsubdomain likewise (i.e.www.example.com). When finished, click the "Generate" button.
cPanel "Create New Certificate Signing Request" form (View big version) - The new CSR volition exist generated, and you will become a confirmation screen:

cPanel CSR confirmation (View big version) - If you go dorsum to the "Certificate Signing Request" home, y'all will see your new CSR listed:

cPanel "Certificate Signing Request" with the new CSR generated (View large version)
Linux, FreeBSD
Brand certain OpenSSL is installed. You can check past using:
openssl version If information technology's not already present, open the command line and install it for your platform:
-
Debian, Ubuntu and clones
sudo apt-get install openssl -
Red Hat, CentOS and clones
sudo yum install openssl -
FreeBSD
make -C /usr/ports/security/openssl install clean
Then, generate a private fundamental and a CSR with a single command:
openssl req -newkey rsa:2048 -nodes -keyout case.com.key -out example.com.csr The private key will be generated, and you will be asked some information for the CSR:
Generating a 2048 fleck RSA private key ........................+++ ................................................................+++ writing new private central to 'example.com.key' ----- You lot are about to exist asked to enter data that will be incorporated into your certificate asking. What yous are almost to enter is what is called a Distinguished Name or a DN. In that location are quite a few fields but you can get out some blank For some fields in that location will be a default value, If you enter '.', the field will be left blank. Answer all questions correctly (they will exist public in your signed certificate!), paying special attention to the "Common Name" section (for example, server FQDN or YOUR proper name), which should exactly match the domain name for which you are requesting the HTTPS certificate. Include the height-level domain only (example.com), the CA volition ordinarily add the www subdomain besides (i.e. www.case.com):
Country Name (2 letter of the alphabet code) [AU]:GB State or Province Name (full name) [Some-Country]:London Locality Proper noun (eg, city) []:London System Name (eg, visitor) [Net Widgits Pty Ltd]:ACME Inc. Organizational Unit of measurement Name (eg, section) []:IT Common Name (e.g. server FQDN or YOUR name) []:example.com E-mail Address []:admin@example.com Please enter the post-obit 'actress' attributes to be sent with your document request A challenge password []: An optional visitor name []: Internet Data Server (IIS) on Windows
- Open "Offset" → "Administrative Tools" → "Cyberspace Information Services (IIS) Managing director." Click the server name. Double-click "Server Certificates" in the middle cavalcade:

Open "Internet Information Services (IIS) Director." Double-click "Server Certificates." (View large version) - Click "Create Certificate Request" in the correct cavalcade.

Click "Create Certificate Request" in the correct column. (View large version) - Enter your organization's details, paying special attention to "Common Name," which should match your domain name. Click "Adjacent."

Enter your system'due south details. (View large version) - Leave the default "Cryptographic Service Provider." Set the "Bit length" to
2048. Click "Adjacent."
Fix the "Bit length" to 2048. (View large version) - Scan for a place to save the generated CSR and click "Finish."

Scan for a identify to save the generated CSR and click 'Cease'. (View large version)
Step 2: Obtaining The HTTPS Certificate
In order to become your website document, showtime purchase a HTTPS certificate credit of a called type (DV, OV, EV, single site, multisite, wildcard — see to a higher place) from an HTTPS certificate provider. Once the procedure is complete, you will accept to provide the certificate signing asking, which will spend the purchased credit for your chosen domain. You'll exist asked to provide (i.e. to paste in a field or to upload) the whole CSR text, including the —–Brainstorm CERTIFICATE Asking—– and —–END Document REQUEST—– lines. If you would like to take an EV or OV certificate, y'all'll demand to provide the legal entity for which yous're requesting the document — you might also exist asked to provide additional documents to confirm that y'all correspond this company. The certificate registrar volition then verify your request (and any supporting documents) and consequence the signed HTTPS certificate.
We've partnered with InMotion Hosting to bring you a great price on their fast and reliable hosting services. InMotion Hosting provides a free AutoSSL for all of your websites to accept HTTPS and they make it very easy to install. Click hither or anywhere that says shared hosting in this commodity to check out their plans and get started!
Getting an HTTPS Certificate
Your hosting provider or HTTPS registrar might have a unlike product and registration procedure, but the general logic should be similar.
- Detect an HTTPS document vendor.
- Select a type of certificate (DV, OV, EV, unmarried site, multisite, wildcard), and click "Add to cart." Specify your preferred payment method and consummate the payment.
- Activate the new HTTPS document for your domain. You tin either paste or upload the certificate signing request. The system will excerpt the document details from the CSR.
- You lot will be asked to select a method of "Domain Control Validation" — whether by email, uploading an HTML file (HTTP-based) or adding a
TXTrecord to your domain zone file (DNS-based). Follow the instructions for your DCV method of pick to validate. - Wait several minutes until the validation is performed and the HTTPS document is issued. Download the signed HTTPS document.
Cocky-Signed Certificates
It is likewise possible to sign a document yourself, rather than take a document authority do it. This is good for testing purposes considering information technology will be cryptographically as good as any other document, but it volition non be trusted by browsers, which volition fire a security warning — yous tin claim you are anything you want, just it wouldn't be verified past a trusted tertiary political party. If the user trusts the website, they could add an exception in their browser, which would store the certificate and trust it for future visits.
The example certificate above is a cocky-signed 1 — you lot can use it for the domain example.com, and it will piece of work within its validity period.
You tin create a self-signed certificate on whatsoever platform that has OpenSSL bachelor:
openssl x509 -signkey example.com.key -in example.com.csr -req -days 365 -out example.com.crt Once the certificate is bachelor, you volition take to install information technology on your server. If y'all are using hosting and HTTPS registration services from the same provider (many hosting providers likewise sell HTTPS certificates), there might exist an automated procedure to install and enable your newly obtained HTTPS document for the website. If you are hosting your website elsewhere, yous will need to download the certificate and configure your server to utilise it.
Stride 3: Installing The HTTPS Certificate For Your Website
cPanel
- Go back to the "SSL/TLS Manager" home. Click "Certificates (CRT)" to import the new certificate.

cPanel "SSL/TLS Manager" (View large version) - You lot will exist redirected to a page to "Paste, Upload or Generate" a new "Certificate." Paste the contents of the document file received from the HTTPS registrar or upload it using the "Browse" push.

cPanel "Import" a new HTTPS certificate (View large version) - When y'all paste the contents of the HTTPS certificate, it will exist parsed, and obviously text values will be presented to you for confirmation. Review the contents and click the "Save Certificate" button.

cPanel "Review" and ostend HTTPS certificate (View big version) - The new HTTPS certificate will be saved, and y'all will get a confirmation screen:

cPanel HTTPS certificate confirmation (View large version) - If you get back to the "Certificates (CRT)" domicile, y'all will see your new HTTPS certificate listed:

cPanel "Certificates" with the new HTTPS certificate listed (View big version) - Become back to the "SSL/TLS Manager" dwelling house. Click "Install and Manage SSL for your website (HTTPS)" to assign the new certificate to your existing website.

cPanel "SSL/TLS Manager" (View big version) - You will exist presented with the "Install an SSL Website" form. Click the "Browse Certificates" push button and select your HTTPS document. Select your website domain from the dropdown list (if it'south not automatically selected), and verify that the fields for "Document" and "Private Key" are populated.

cPanel "Install an SSL Website" (View large version)
Exam to come across that you can access your website at the address https://www.instance.com. If all works OK, yous will most probably want to permanently redirect your HTTP traffic to HTTPS. To practise so, you'll have to include several lines of lawmaking to an .htaccess file (if you're using an Apache web server) in your website'south root folder:
RewriteEngine On RewriteCond %{HTTPS} off RewriteRule ^(.*)$ https://%{HTTP_HOST}%{REQUEST_URI} [L,R=301] If the .htaccess file already exists, then paste the RewriteCond and RewriteRule lines only, correct later on the existing RewriteEngine On directive.
Linux, FreeBSD
Place the generated private key (example.com.key), Certificate Signing Asking (example.com.csr) and the valid HTTPS document (example.com.crt) in the appropriate locations:
-
Debian, Ubuntu and clones, FreeBSD
cp case.com.crt /etc/ssl/certs/ cp example.com.primal /etc/ssl/private/ cp instance.com.csr /etc/ssl/individual/ -
Red Chapeau, CentOS and clones
cp example.com.crt /etc/pki/tls/certs/ cp example.com.key /etc/pki/tls/private/ cp example.com.csr /etc/pki/tls/private/ restorecon -RvF /etc/pki
The files should be owned by root and protected by a permission setting of 600.
-
Debian, Ubuntu and clones
chown -R root. /etc/ssl/certs /etc/ssl/individual chmod -R 0600 /etc/ssl/certs /etc/ssl/private -
Carmine Chapeau, CentOS and clones
chown -R root. /etc/pki/tls/certs /etc/pki/tls/private chmod -R 0600 /etc/pki/tls/certs /etc/pki/tls/private -
FreeBSD
chown -R root:bike /etc/ssl/certs /etc/ssl/private chmod -R 0600 /etc/ssl/certs /etc/ssl/private
Apache
To enable the HTTPS version of your website, yous should:
- brand sure that mod_ssl is installed on your server,
- upload the received HTTPS certificate (
.crt) file to your server, - edit the Apache server configuration files.
Start by checking mod_ssl. Depending on your operating arrangement, either ane should work:
apache2 -M | grep ssl or httpd -M | grep ssl If mod_ssl is installed, yous should go either this…
ssl_module (shared) Syntax OK … or something similar.
If it's not present or non enabled, so try this:
-
Debian, Ubuntu and clones
sudo a2enmod ssl sudo service apache2 restart -
Reddish Hat, CentOS and clones
sudo yum install mod_ssl sudo service httpd restart -
FreeBSD (select the SSL option)
make -C /usr/ports/www/apache24 config install make clean apachectl restart
Edit the Apache configuration file (httpd.conf):
- Debian, Ubuntu
/etc/apache2/apache2.conf - Crimson Hat, CentOS
/etc/httpd/conf/httpd.conf - FreeBSD
/usr/local/etc/apache2x/httpd.conf
Mind lxxx Listen 443 <VirtualHost *:80> ServerName instance.com ServerAlias world wide web.example.com Redirect 301 / https://world wide web.instance.com/ </VirtualHost> <VirtualHost *:443> ServerName case.com Redirect 301 / https://www.example.com/ </VirtualHost> <VirtualHost *:443> ServerName www.example.com ... SSLEngine on SSLCertificateFile/path/to/signed_certificate_followed_by_intermediate_certs SSLCertificateKeyFile /path/to/private/fundamental # Uncomment the following directive when using client document authentication #SSLCACertificateFile /path/to/ca_certs_for_client_authentication # HSTS (mod_headers is required) (15768000 seconds = 6 months) Header always set Strict-Transport-Security "max-historic period=15768000" ... </VirtualHost> # intermediate configuration, tweak to your needs SSLProtocol all -SSLv3 SSLCipherSuite ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA:ECDHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES256-SHA:ECDHE-ECDSA-DES-CBC3-SHA:ECDHE-RSA-DES-CBC3-SHA:EDH-RSA-DES-CBC3-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:DES-CBC3-SHA:!DSS SSLHonorCipherOrder on SSLCompression off SSLSessionTickets off # OCSP Stapling, only in httpd 2.3.3 and later SSLUseStapling on SSLStaplingResponderTimeout 5 SSLStaplingReturnResponderErrors off SSLStaplingCache shmcb:/var/run/ocsp(128000) This configuration was generated using the Mozilla SSL Configuration Generator, mentioned earlier. Check with information technology for an up-to-date configuration. Make sure to edit the paths to the certificate and private key. The configuration provided was generated using the intermediate setting — read the limitations and supported browser configurations for each setting to decide which ane suits you best.
Some modifications to the generated code were made (marked in bold higher up) to handle redirects from HTTP to HTTPS, as well every bit not-world wide web to the www domain (useful for SEO purposes).
nginx
Edit the nginx configuration file (nginx.conf):
- Debian, Ubuntu, Red Hat, CentOS
/etc/nginx/nginx.conf - FreeBSD
/usr/local/etc/nginx/nginx.conf
server { listen 80 default_server; heed [::]:80 default_server; # Redirect all HTTP requests to HTTPS with a 301 Moved Permanently response. render 301 https://$host$request_uri; } server { heed 443 ssl http2; listen [::]:443 ssl http2; # certs sent to the customer in SERVER Hello are concatenated in ssl_certificate ssl_certificate /path/to/signed_cert_plus_intermediates; ssl_certificate_key /path/to/private_key; ssl_session_timeout 1d; ssl_session_cache shared:SSL:50m; ssl_session_tickets off; # Diffie-Hellman parameter for DHE ciphersuites, recommended 2048 bits ssl_dhparam /path/to/dhparam.pem; # intermediate configuration. tweak to your needs. ssl_protocols TLSv1 TLSv1.1 TLSv1.two; ssl_ciphers 'ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA:ECDHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES256-SHA:ECDHE-ECDSA-DES-CBC3-SHA:ECDHE-RSA-DES-CBC3-SHA:EDH-RSA-DES-CBC3-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:DES-CBC3-SHA:!DSS'; ssl_prefer_server_ciphers on; # HSTS (ngx_http_headers_module is required) (15768000 seconds = 6 months) add_header Strict-Send-Security max-historic period=15768000; # OCSP Stapling --- # fetch OCSP records from URL in ssl_certificate and cache them ssl_stapling on; ssl_stapling_verify on; ## verify concatenation of trust of OCSP response using Root CA and Intermediate certs ssl_trusted_certificate /path/to/root_CA_cert_plus_intermediates; resolver <IP DNS resolver>; .... } This configuration was generated using the Mozilla SSL Configuration Generator, mentioned earlier. Bank check with it for an up-to-date configuration. Make certain to edit the paths to the certificate and private key. The configuration provided was generated using the intermediate setting — read the limitations and supported browser configurations for each setting to decide which 1 suits yous best.
The generator automatically generates lawmaking for handling redirects from HTTP to HTTPS, and information technology enables HTTP/two out of the box!
Cyberspace Information Server (IIS) on Windows
- Open "Start" → "Administrative Tools" → "Internet Data Services (IIS) Manager." Click the server proper name. Double-click "Server Certificates" in the middle cavalcade:

Open "Net Information Services (IIS) Manager." Double-click "Server Certificates." (View large version) - Click "Complete Document Asking" in the right column.

Click "Complete Certificate Request" in the correct cavalcade. (View large version) - Select the signed certificate file (
example.com.crt) that you obtained from the CA. Enter some name in the "Friendly proper noun" field to be able to distinguish the certificate later. Place the new certificate in the "Personal" document shop (IIS 8+). Click "OK."
Select the signed document file. (View large version) - If the process went OK, y'all should run across the certificate listed nether "Server Certificates."

Y'all should run across the certificate listed under "Server Certificates." (View large version) - Expand the server name. Nether "Sites," select the website to which you want to assign the HTTPS certificate. Click "Bindings" from the right column.

Select the website and click "Bindings." (View large version) - In the "Site bindings" window, click the "Add" button.

Click the "Add" button. (View large version) - In the new window, select:
- "Type": "https"
- "IP address": "All Unassigned"
- "Port": "443"
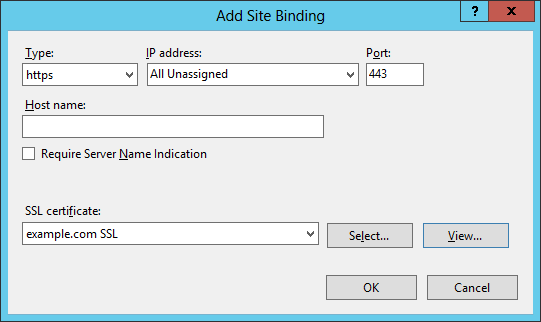
Select "HTTPS," and select the installed HTTPS certificate. (View large version) - You should now take both HTTP and HTTPS installed for this website.
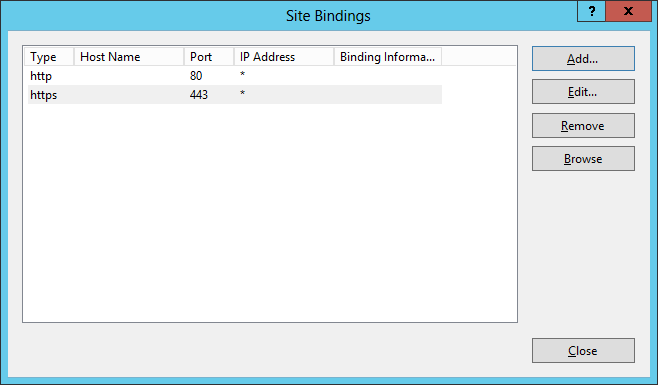
You should at present have both HTTP and HTTPS installed for this website. (View large version)
Mixed-Content Warnings
Yous might get a warning sign next to the address bar and a message such every bit "Connection is not secure! Parts of this page are not secure (such as images)." This does not mean that your installation is wrong; just make certain that all links to resources (images, style sheets, scripts, etc.), whether local or from remote servers, practice non start with https://. All resource should be pointed to with paths relative to the root (/images/image.png, /styles/style.css, etc.) or relative to the electric current document (../images/paradigm.png), or they should exist full URLs outset with https://, such equally <script src="https://code.jquery.com/jquery-three.1.0.min.js"></script>.
These tips should eliminate the mixed-content warnings, and your browser should display the closed padlock without an exclamation mark.
Testing Your Server
Later on you accept configured your server and take the website upward and running on HTTPS, I strongly recommend checking its security configuration using the Qualys SSL Server Test. This performs a scan of your website, including a comprehensive evaluation of its configuration, possible weaknesses and recommendations. Follow the communication at that place to further improve your server's security configuration.
Renewal
Your certificate is valid for a ready period — typically, a year. Don't wait to renew information technology at the terminal moment — your registrar volition starting time sending you lot emails as the renewal engagement approaches. Exercise effect a new certificate as soon as you go your outset reminder. The procedure is pretty much the same: Create a new certificate signing request, get a new HTTPS certificate, and install information technology on your server. The document's validity will first running at the time of signing, while the expiration volition exist set one twelvemonth later your electric current certificate expires. Thus, there will be a time when both your old and new certificates will be valid, and so a full new year later on the expiration of the old certificate. During the overlap, you will be able to make sure that the new certificate is working OK, before the quondam one expires, assuasive for uninterrupted service of your website.
Revocation
If your server is compromised or if y'all recollect someone might have access to your private central, yous should immediately revoke your current HTTPS document. Different registrars have different procedures, but it generally boils downwards to marking the compromised certificate every bit inactive in a special database of your registrar, and and then issuing a new HTTPS certificate. Of class, revoke the current document as before long as possible, and then that nobody can impersonate you, and get the new document only subsequently you lot take investigated and stock-still the crusade of the security alienation. Please ask your registrar for assistance.
Let's Encrypt
To quote the Let's Encrypt website:
Let's Encrypt is a free, automated, and open document authority (CA), run for the public'due south benefit. Let's Encrypt is a service provided by the Internet Security Research Group (ISRG).The primal principles behind Allow's Encrypt are:
- Free Anyone who owns a domain proper name tin can use Permit'southward Encrypt to obtain a trusted document at zero price.
- Automatic Software running on a web server can interact with Permit's Encrypt to painlessly obtain a certificate, securely configure it for use, and automatically have care of renewal.
- Secure Let's Encrypt will serve as a platform for advancing TLS security best practices, both on the CA side and by helping website operators properly secure their servers.
- Transparent All certificates issued or revoked will exist publicly recorded and available for anyone to inspect.
- Open up The automated issuance and renewal protocol will be published equally an open up standard that others can adopt.
- Cooperative Much similar the underlying Internet protocols themselves, Let'southward Encrypt is a joint attempt to benefit the community, beyond the command of any one organization.
To take advantage of Permit'southward Encrypt, set up up your hosting account or server properly. Let's Encrypt offers curt-term certificates that need to be renewed regularly in lodge to keep an HTTPS website operational.
How It Works
There are some substantial differences in the style of operation between Allow's Encrypt and the other CAs. Following the starting time three points above, hither are the primary ones:
- Free. The Let'due south Encrypt HTTPS certificates are completely free for the whole lifespan of your website.
- Automatic. The Let's Encrypt HTTPS certificates are valid for 90 days, dissimilar regular HTTPS certificates, which are valid for one year. People are encouraged to automate their certificate renewal; for case, the administrator of the server would set up a dedicated software service (or would periodically invoke software from cron) to manage the initial domain validation and subsequent renewal for all hosted domains — gear up-it-and-forget-it style.
- Secure. Let's Encrypt HTTPS certificates are issued with no compromise on security, leading to sure incompatibilities with older and more exotic platforms. Cheque the compatibility page to determine whether yous are fine cutting off incompatible platforms.
Limitations
Allow'south Encrypt provides just DV certificates. OV and EV are non supported, and there are currently no plans to support them. Unmarried- and multiple-domain HTTPS certificates are offered, but no wildcard ones at the moment. Run into the Let's Encrypt FAQ for more information.
Let'southward Encrypt's automated mode of operation enforces some usage limits in order to protect the infrastructure from intentional and unintentional abuse. The rate limits are high enough non to affect regular users with even hundreds of domains. However, if yous manage HTTPS certificates at a very big scale, yous might want to check them out.
Older and exotic clients (prior to Windows XP SP3) are not supported. Check the compatibility page for details.
Using The Let's Encrypt HTTPS Certificates In Exercise
cPanel
- Log into your host's cPanel
- Coil downward to the "Security" section, and click "Let'southward Encrypt for cPanel."

cPanel "Security" section (View large version) - Y'all are now in the "Let's Encrypt for cPanel" section. Check both domain names (
instance.comandwww.example.com), and click "Consequence Multiple."
Check both domain names and click "Event Multiple." (View large version) - You lot will exist taken to a confirmation screen. Your top-level (i.e. not-
www) domain name will exist selected equally the primary, and yourwwwdomain name as an alias, which will be placed in the HTTPS certificate'south "Subject Alt Name" (SAN) tape. Click "Issue" to continue. Please exist patient and do not refresh the page, because the initial validation might take longer — virtually a minute or 2.
Click "Issue" and be patient for most a infinitesimal or two. (View big version) - If the procedure completes successfully, y'all volition see a confirmation message. Click "Become back" to see the installed HTTPS certificate.

If the process completes successfully, y'all will see a confirmation bulletin. (View large version) - Y'all will see your domain listed nether "Your domains with Allow's Encrypt certificates." Y'all may check the certificate's details and verify that the website opens with the
https://prefix in your browser.
Your domains with Allow'southward Encrypt certificates (View large version)
Linux, FreeBSD, Other
The easiest manner to gear up Let's Encrypt on your server is with Certbot. Just select your web server and operating system and follow the instructions.

Internet Data Server on Windows
There is currently no official client for IIS on Windows, but there are workarounds.
There are several projects to create a native Windows client for Let's Encrypt:
- ACMESharp (PowerShell) is the first endeavour to write a Windows client.
- letsencrypt-win-uncomplicated (for the control line) seems the easiest to use.
- Certify provides a GUI on top of ACMESharp, but is still in alpha.
Cloudflare
Cloudflare is a service that provides a content delivery network (CDN), website security, and protection against distributed denial of service (DDoS) attacks. It features a free HTTPS certificate with all subscription plans, including the free one — a shared DV Cloudflare Universal SSL certificate. In order to have a unique HTTPS certificate, you need to upgrade to the Business plan.
To have advantage, only create an account, set your website, and visit the "Crypto" section.
CertSimple
CertSimple is an EV-simply HTTPS document vendor. It is disrupting the EV HTTPS document market in a way similar to what Permit's Encrypt is doing in the DV HTTPS certificate marketplace, by providing a faster, easier process of organization validation — an otherwise slow and cumbersome routine. Hither are its advantages:
- Simplified application procedure. No software to install or command line questions. Live validation, with most details checked before payment.
- Fast validation fourth dimension. Three hours on boilerplate versus the industry standard 7 to 10 days.
- Free reissues for the lifetime of the certificate. Easily add together domain names later or fix a lost private central.
You lot can read an fantabulous, in-depth review of the process on Troy Hunt's weblog.
Multiple HTTPS Websites On A Single IP Address
Due to the nature of the handshake procedure, virtual hosts with a single IP address are a problem for TLS. Virtual hosts piece of work by having the customer include the domain name as part of the HTTP asking header, but when HTTPS is used, the TLS handshake happens before the HTTP headers are sent — the secure channel should be initialized and fully functional before transmitting whatsoever patently-text HTTP, including headers. So, the server does not know which HTTPS certificate to present up front to a connecting client, so it presents the outset one information technology finds in its configuration file, which, of form, only works correctly for the get-go TLS-enabled website.
There are several workarounds: to have a unique IP for each TLS-enabled domain, or to accept all domains in a single document. Both are impractical — the IPv4 address space is now used upwardly, and having one big HTTPS document ways that if yous want to add a single website to this server, you'll need to reissue the whole multiple-domain certificate.
An extension to the TLS protocol, named Server Proper name Indication (SNI), was introduced to overcome this limitation. Both servers and clients should support information technology, and although SNI support is present widely available, information technology is still not 100% impenetrable, if compatibility with all possible clients is a requirement.
You can read more about running SNI for Apache, nginx and IIS (eight+) in the corresponding documentation.
Useful Resource
- Mozilla SSL Configuration Generator
- SSL Server Test, Qualys
- "Security/Server Side TLS," Mozilla wiki
- "SSL and TLS Deployment Best Practices," SSL Labs
- Documentation, Qualys SSL Labs
- "Database Search and Replace Script in PHP," Interconnect IT For replacing all instances of HTTP with HTTPS (links, images, etc.) in a WordPress database.
- Chrome and Firefox explicitly mark websites that provide forms on pages without HTTPS equally being non-secure.
- HTTPS has go an SEO ranking gene,
- HTTPS has a serious privacy impact.
![]() (rb, vf, cm, al, il)
(rb, vf, cm, al, il)
Source: https://www.smashingmagazine.com/2017/06/guide-switching-http-https/
Post a Comment for "If I Upload a Page From a Non Https to My Domain Which Is Https Will I Still Be Secure"